DNS queries
ThreatLockDown has default rules for DNS queries made to a private DNS handled by the Google Cloud DNS service. Those logs can be collected using the gcp-pubsub module. Details on how to configure the module can be found in the gcp-pubsub configuration reference.
Configure Google DNS logs collection
To collect the DNS queries made to the Google DNS service it is necessary to enable DNS logging. To do that, follow the Google Cloud DNS logging guide.
Once DNS Cloud logging is configured, the generated logs must be ingested into a Pub/Sub topic so that ThreatLockDown can collect them using the Pub/Sub integration. To achieve that, it is necessary to define a custom log router.
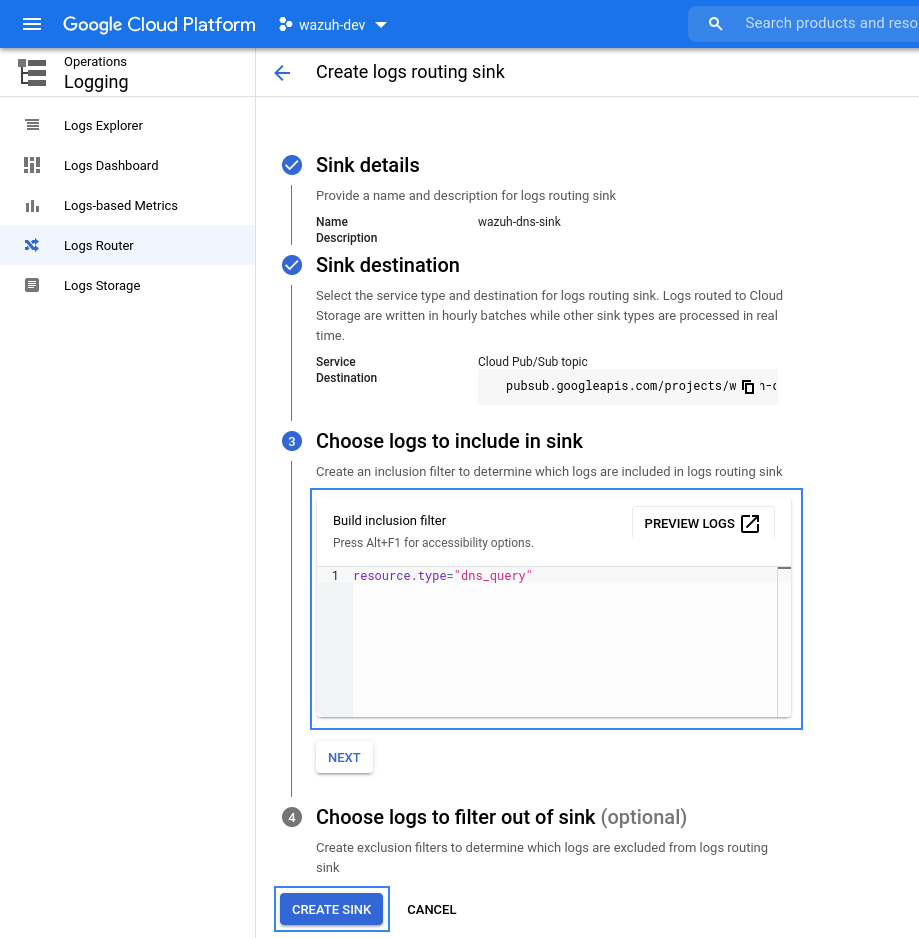
Visit the Google Cloud Logging section and click on CREATE SINK.
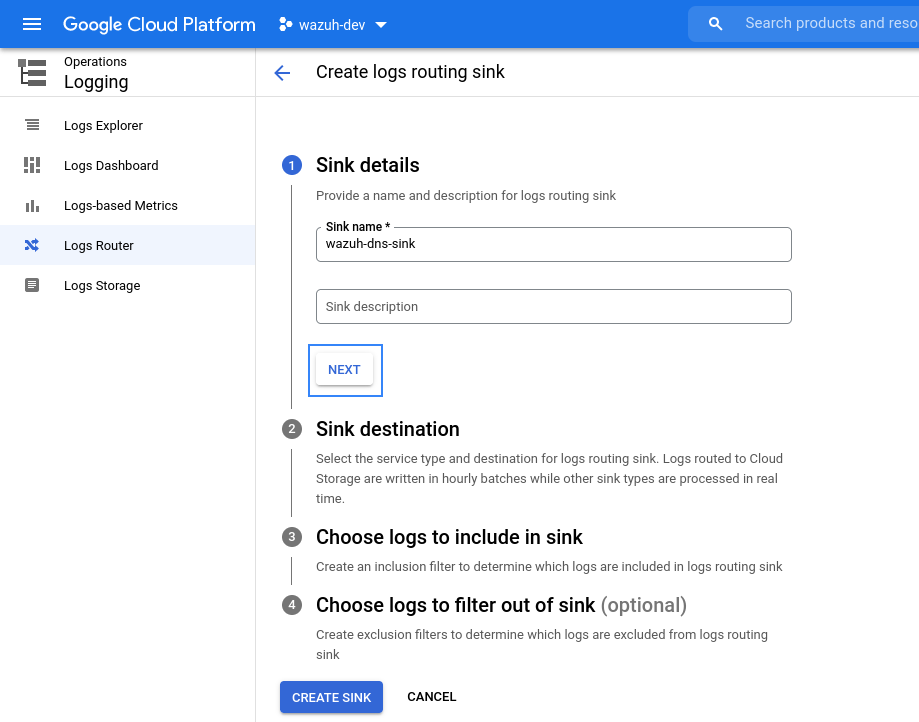
Provide a descriptive name for the sink and click on NEXT.
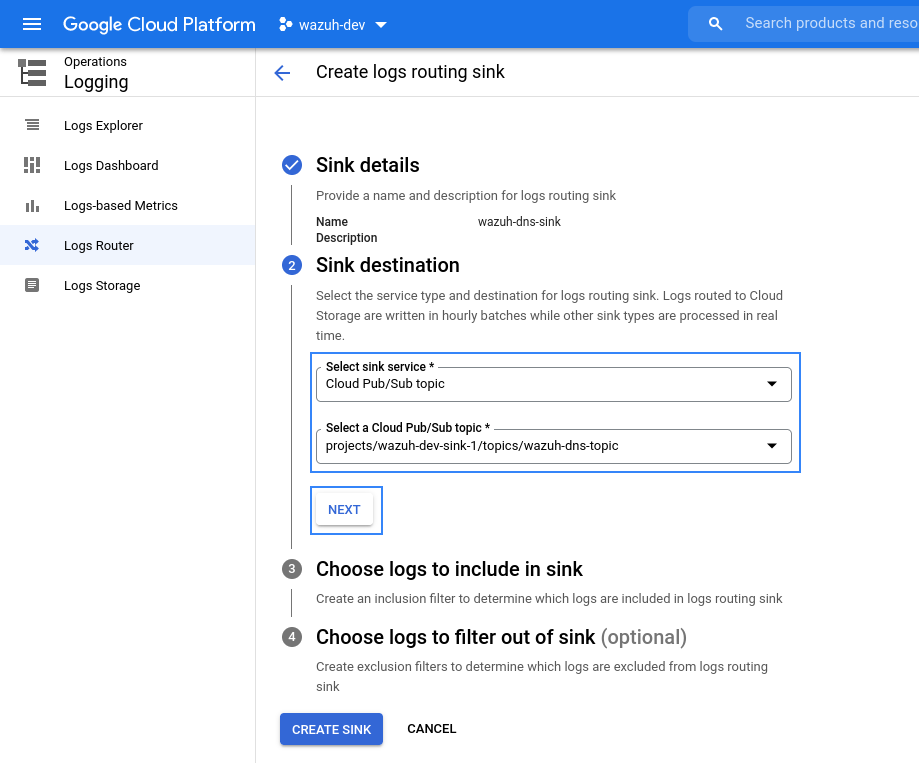
Once the name for the sink is chosen, it is necessary to select the sink destination. As sink service, choose Cloud Pub/Sub topic, and then create or choose a topic to be used as destination. Then click on NEXT.
Use the following query to collect all the DNS queries.
resource.type = "dns_query"
If it is not necessary to filter any logs out of the sink, click on CREATE SINK.
Once this process is finished, you can configure the ThreatLockDown GCP Pub/Sub integration to process the audit logs of the selected resources as usual.
ThreatLockDown dashboard visualization
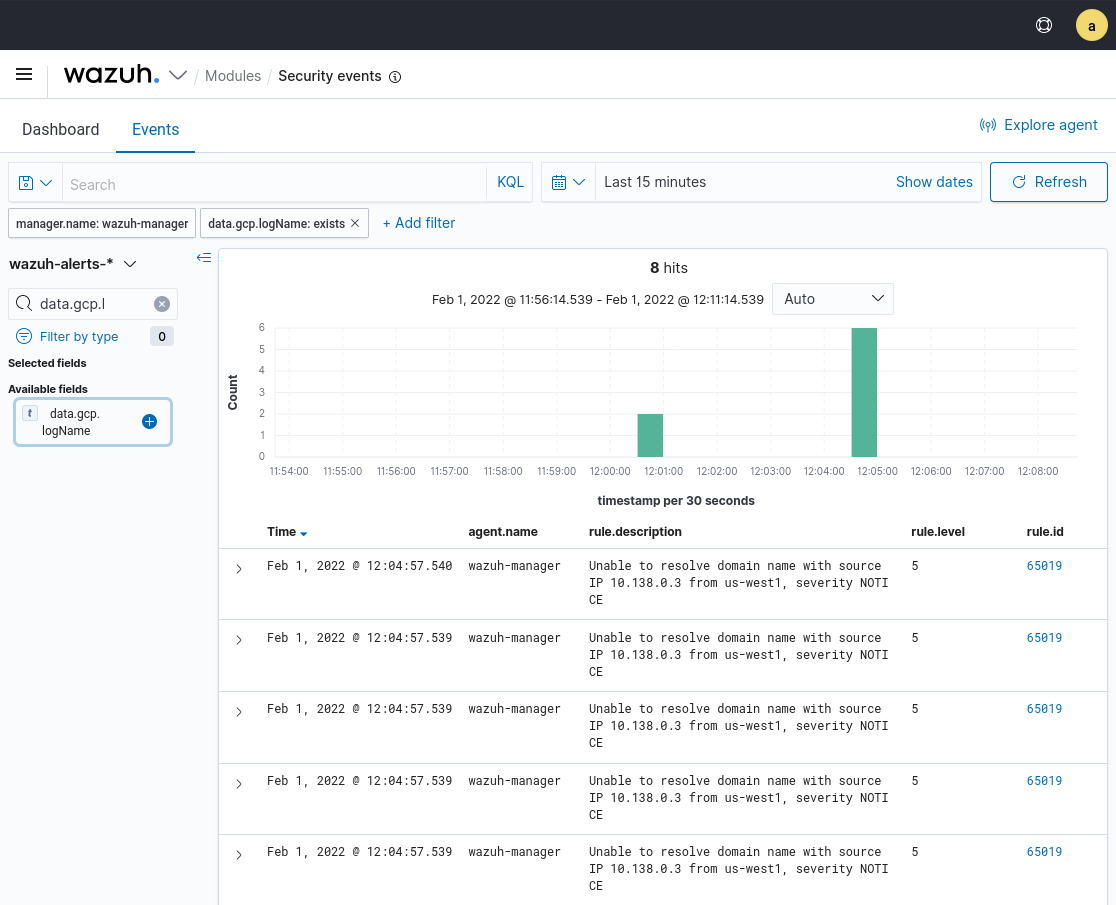
After configuring the GCP Pub/Sub module to fetch the DNS logs from Google Cloud, it is possible to visualize the alerts generated in the ThreatLockDown dashboard.
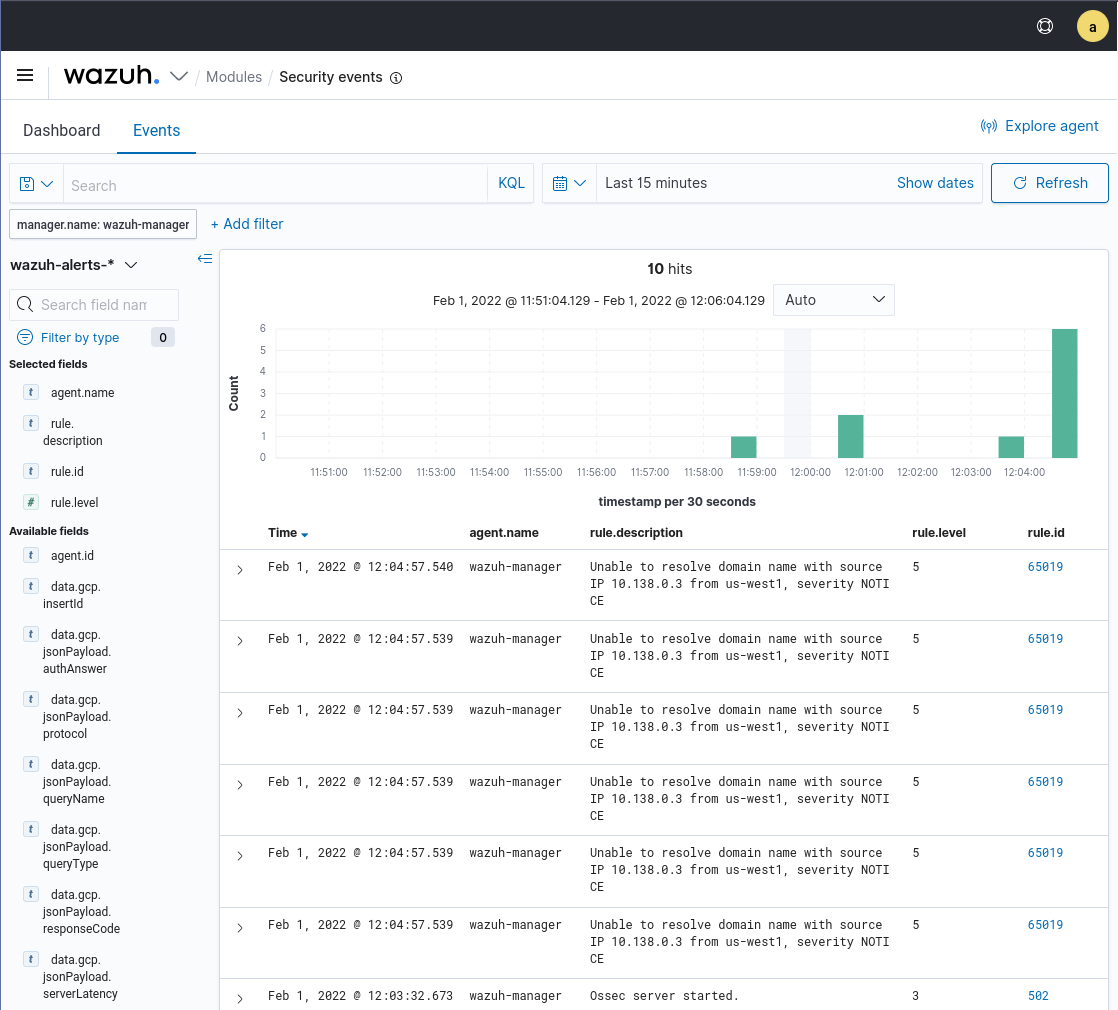
Google Cloud logs can be filtered by the data.gcp.logName field:
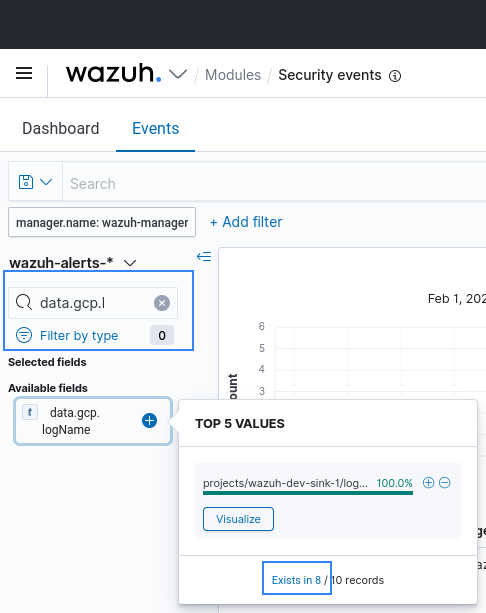
After selecting the Exists in button, only Google Cloud-related events will appear in the ThreatLockDown dashboard.