Vulnerability detection
Software vulnerabilities are weaknesses in code that can allow attackers to gain access to or manipulate the behavior of an application. Vulnerable software applications are commonly targeted by attackers to compromise endpoints and gain a persistent presence on targeted networks.
Vulnerability detection is the process of identifying these flaws before they are discovered and exploited by attackers. The goal of vulnerability detection is to identify vulnerabilities so that remediation can be carried out to prevent successful attacks.
The ThreatLockDown agent uses the Syscollector module to collect inventory details from the monitored endpoint. It sends the collected data to the ThreatLockDown server. Within the ThreatLockDown server, the Vulnerability Detection module correlates the software inventory data with vulnerability content documents to detect vulnerable software on the monitored endpoint.
ThreatLockDown detects vulnerable applications, generating risk reports, using our Cyber Threat Intelligence (CTI) platform. In this platform, we aggregate vulnerability data from diverse sources like operating system vendors and vulnerability databases, consolidating it into a unified, reliable repository. The process involves standardizing the varied formats into a common structure. Additionally, we maintain the integrity of our vulnerability data by doing the following.
Rectifying format inconsistencies like version errors and typos.
Completing missing information.
Incorporating new cybersecurity vulnerabilities.
Subsequently, we merge this content, uploading the compiled documents to a cloud server. Finally, we publish these documents to our CTI API.
Relying on the ThreatLockDown CTI, the Vulnerability Detection module supports a variety of operating systems, such as Windows, CentOS, Red Hat Enterprise Linux, Ubuntu, Debian, Amazon Linux, Arch Linux, and macOS operating systems, and applications.
Achieve comprehensive visibility
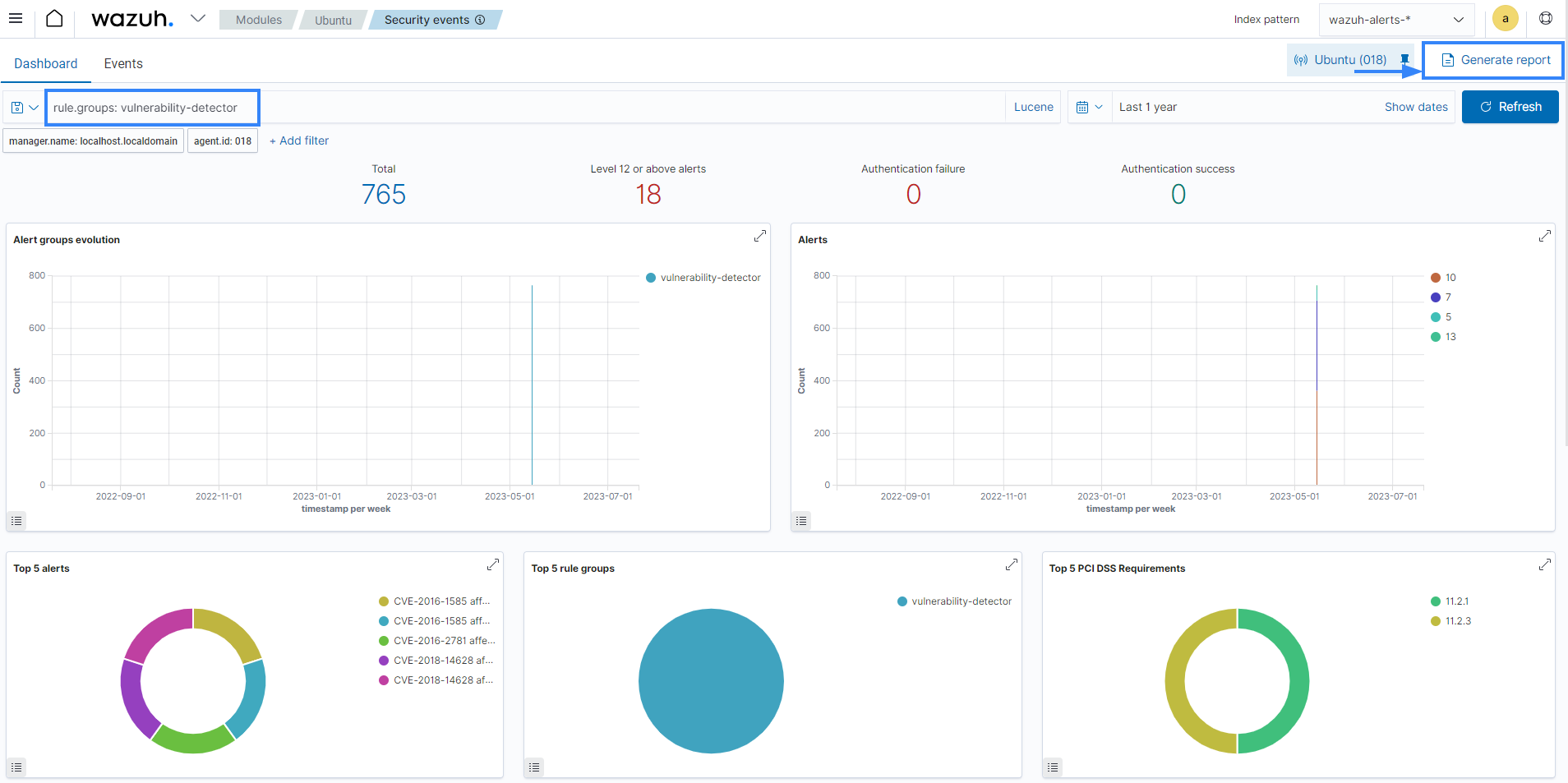
The Vulnerability Detection module generates alerts for vulnerabilities discovered on the operating system and applications installed on the monitored endpoint. It correlates the software inventory collected by the ThreatLockDown agent with the vulnerability content documents and displays the alert generated on the ThreatLockDown dashboard. This provides a clear and comprehensive view of vulnerabilities identified in all monitored endpoints, allowing you to view, analyze and fix vulnerabilities.
The vulnerability detection dashboard shows the frequency of occurrences in different categories such as package name, operating system, agent name, vulnerability ID, and alert severity. This allows analysts to direct their focus appropriately.
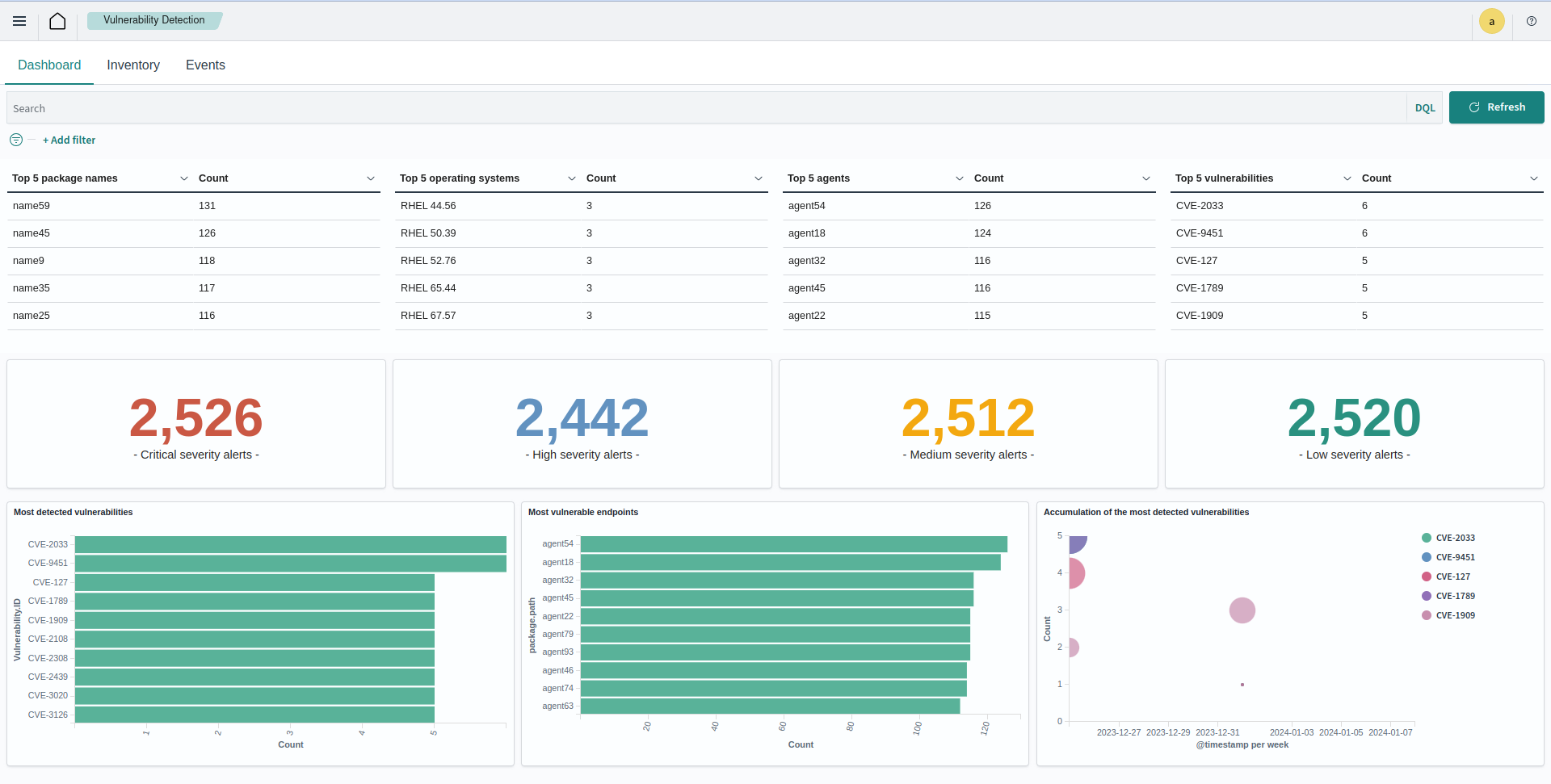
You can view the alerts generated on the dashboard when new vulnerabilities are discovered.
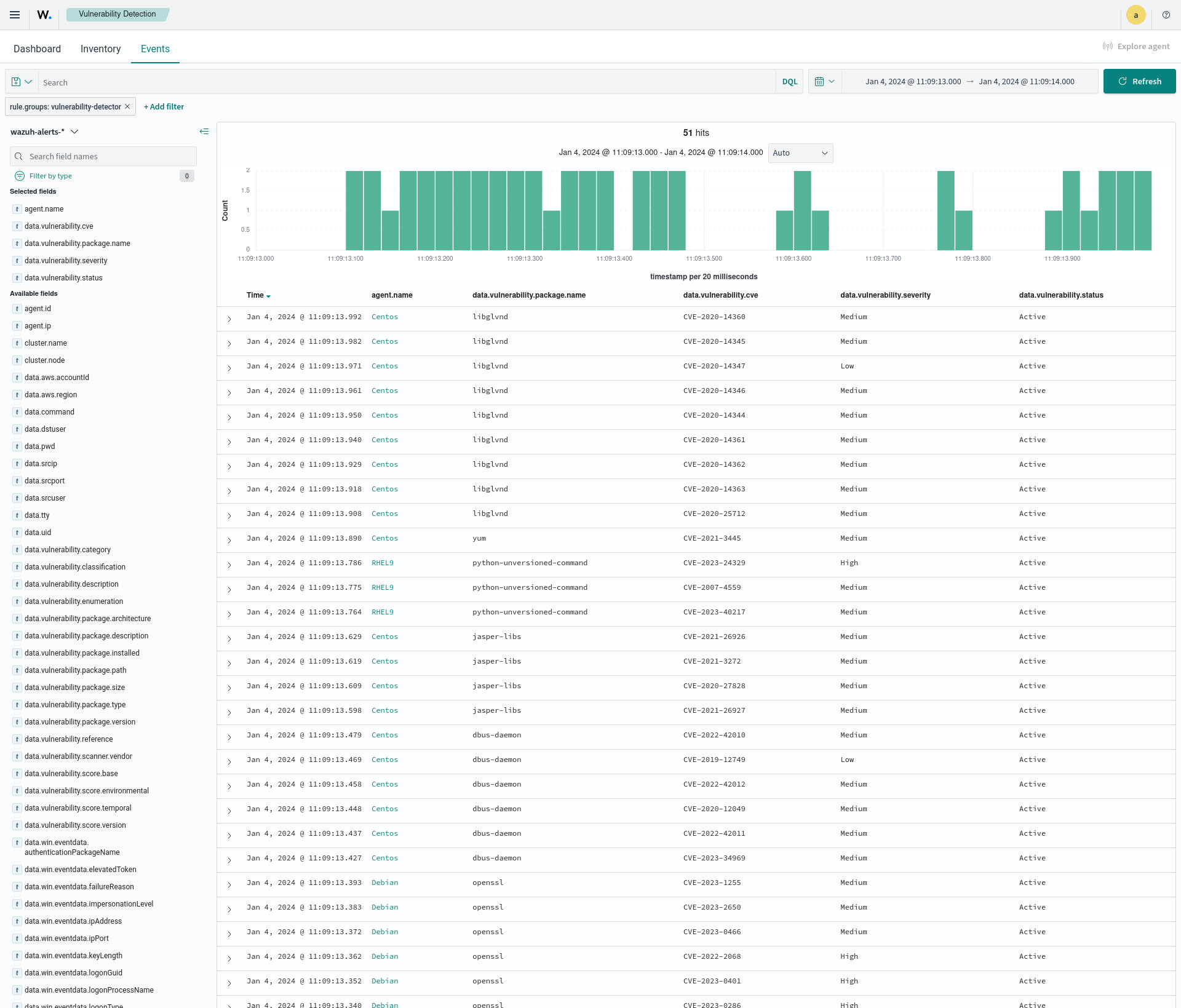
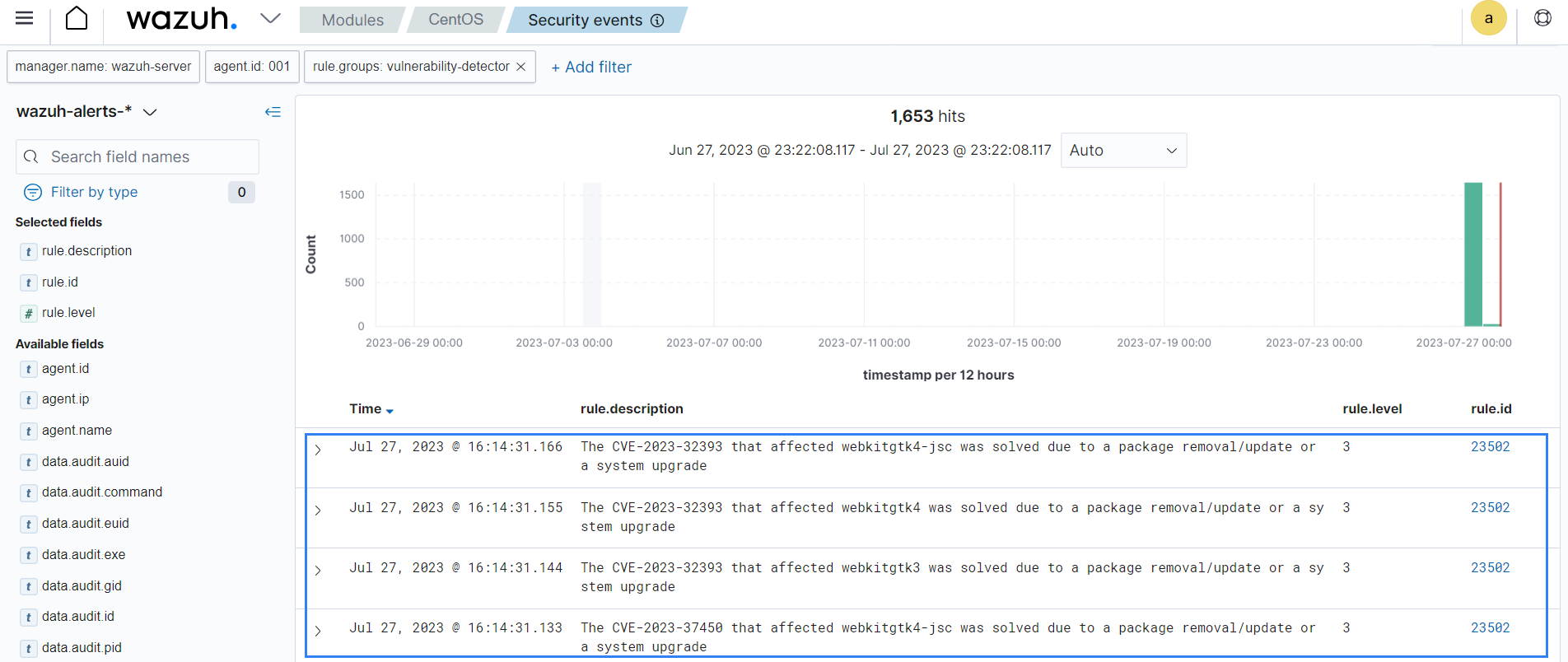
The alerts generated on the dashboard could also be a result of remediation activities. The image below shows alerts generated after an upgrade or an uninstallation of a package resolved a vulnerability.
Obtain actionable intelligence from vulnerability alerts
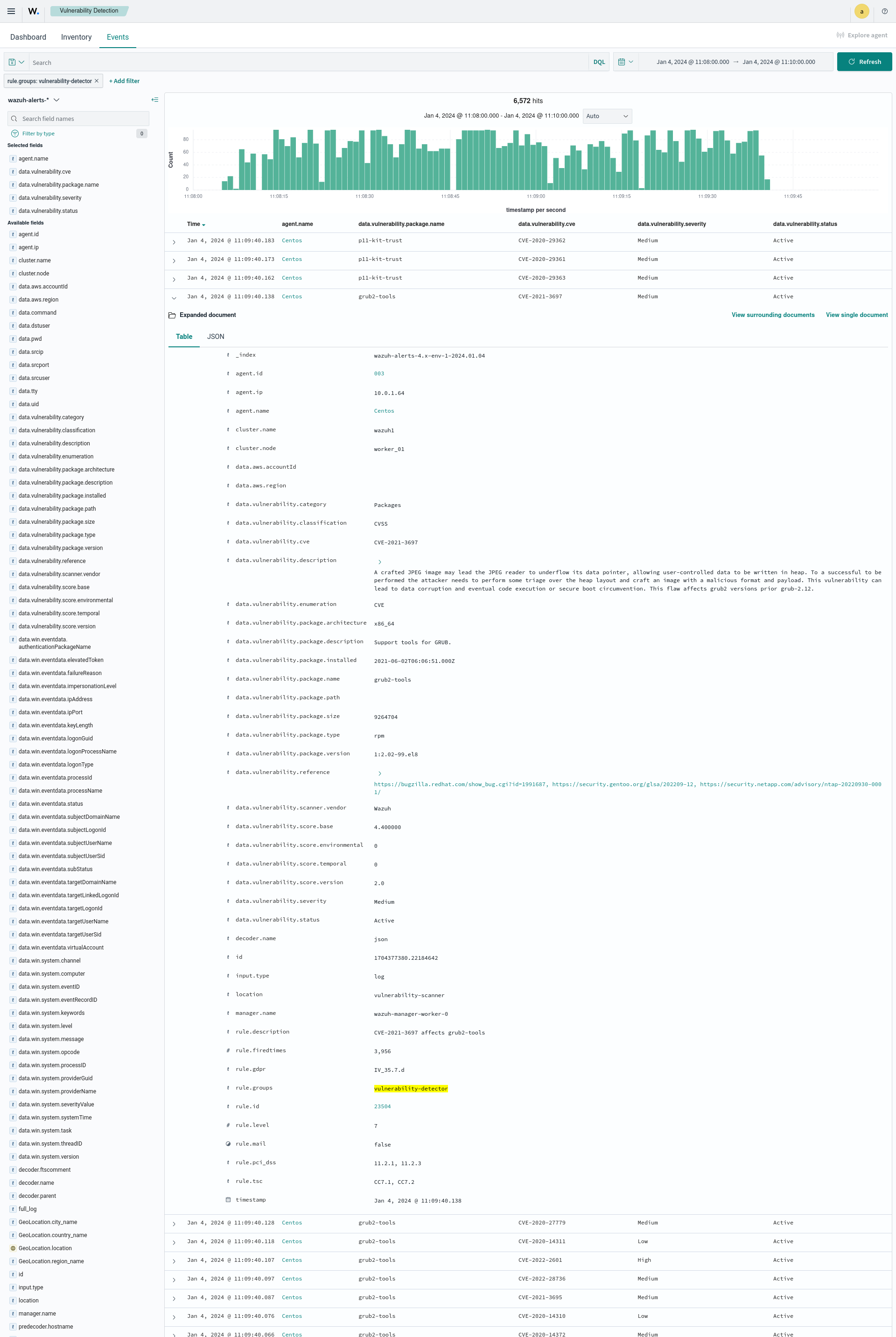
ThreatLockDown vulnerability alerts contain relevant information about the identified vulnerability which can help users understand and decide on remediation steps. You can see an example of a vulnerability detection alert below:
{
"_index": "wazuh-alerts-4.x-env-1-2024.01.04",
"_id": "-1DO1IwBV9gueGHd9CSt",
"_version": 1,
"_score": null,
"_source": {
"cluster": {
"node": "worker_01",
"name": "wazuh1"
},
"input": {
"type": "log"
},
"agent": {
"ip": "10.0.1.64",
"name": "Centos",
"id": "003"
},
"manager": {
"name": "wazuh-manager-worker-0"
},
"data": {
"vulnerability": {
"reference": "https://bugzilla.redhat.com/show_bug.cgi?id=1991687, https://security.gentoo.org/glsa/202209-12, https://security.netapp.com/advisory/ntap-20220930-0001/",
"severity": "Medium",
"score": {
"environmental": "0",
"version": "2.0",
"temporal": "0",
"base": "4.400000"
},
"cve": "CVE-2021-3697",
"package": {
"installed": "2021-06-02T06:06:51.000Z",
"path": " ",
"size": "9264704",
"name": "grub2-tools",
"description": "Support tools for GRUB.",
"type": "rpm",
"version": "1:2.02-99.el8",
"architecture": "x86_64"
},
"scanner": {
"vendor": "Wazuh"
},
"description": "A crafted JPEG image may lead the JPEG reader to underflow its data pointer, allowing user-controlled data to be written in heap. To a successful to be performed the attacker needs to perform some triage over the heap layout and craft an image with a malicious format and payload. This vulnerability can lead to data corruption and eventual code execution or secure boot circumvention. This flaw affects grub2 versions prior grub-2.12.",
"category": "Packages",
"classification": "CVSS",
"enumeration": "CVE",
"status": "Active"
},
"aws": {
"accountId": "",
"region": ""
}
},
"rule": {
"firedtimes": 3956,
"mail": false,
"level": 7,
"pci_dss": [
"11.2.1",
"11.2.3"
],
"tsc": [
"CC7.1",
"CC7.2"
],
"description": "CVE-2021-3697 affects grub2-tools",
"groups": [
"vulnerability-detector"
],
"id": "23504",
"gdpr": [
"IV_35.7.d"
]
},
"location": "vulnerability-scanner",
"decoder": {
"name": "json"
},
"id": "1704377380.22184642",
"timestamp": "2024-01-04T14:09:40.138+0000"
},
"fields": {
"timestamp": [
"2024-01-04T14:09:40.138Z"
]
},
"highlight": {
"rule.groups": [
"@opensearch-dashboards-highlighted-field@vulnerability-detector@/opensearch-dashboards-highlighted-field@"
]
},
"sort": [
1704377380138
]
}
As you can see above, the alert contains key information about the detected vulnerability. This information includes the CVE information, reference links for further research, and a description that provides a concise explanation of the vulnerability.
Track vulnerability remediation
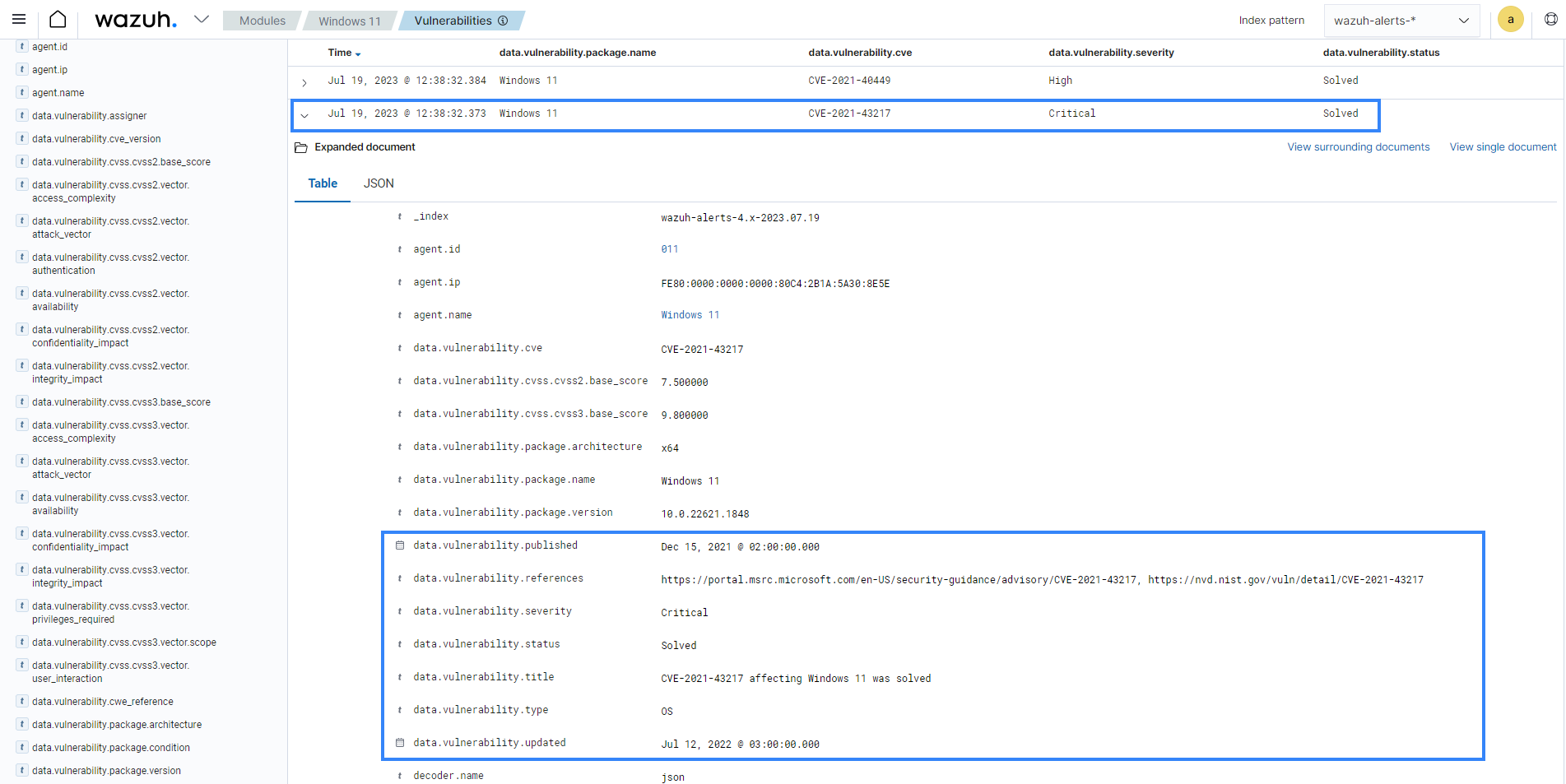
The ThreatLockDown Vulnerability Detection module also allows you to confirm when a vulnerability has been remediated. This feature detects when a patch or software upgrade resolves a previously detected vulnerability. The feature is enabled using the hotfixes option and is available for Windows endpoints.
Use vulnerability reports to identify critical security issues
ThreatLockDown provides users with the ability to download a report that contains security events related to discovered and resolved vulnerabilities. This feature allows users to identify endpoints with unresolved vulnerabilities and keep track of remediation activities.