Configuring vulnerability detection
The Vulnerability Detection module is enabled by default.
The following configuration block shows a configuration example for the Vulnerability Detection module. You can find the Vulnerability Detection settings in the ThreatLockDown server configuration file at /var/ossec/etc/ossec.conf.
<vulnerability-detection>
<enabled>yes</enabled>
<index-status>yes</index-status>
<feed-update-interval>60m</feed-update-interval>
</vulnerability-detection>
<indexer>
<enabled>yes</enabled>
<hosts>
<host>https://0.0.0.0:9200</host>
</hosts>
<username>admin</username>
<password>admin</password>
<ssl>
<certificate_authorities>
<ca>/etc/filebeat/certs/root-ca.pem</ca>
</certificate_authorities>
<certificate>/etc/filebeat/certs/filebeat.pem</certificate>
<key>/etc/filebeat/certs/filebeat-key.pem</key>
</ssl>
</indexer>
The following configuration block shows a configuration example for Syscollector in a Windows endpoint. You can find these settings in the Windows agent configuration file at C:\Program Files (x86)\ossec-agent\ossec.conf.
<!-- System inventory --> <wodle name="syscollector"> <disabled>no</disabled> <interval>1h</interval> <scan_on_start>yes</scan_on_start> <hardware>yes</hardware> <os>yes</os> <network>yes</network> <packages>yes</packages> <hotfixes>yes</hotfixes> <ports all="no">yes</ports> <processes>yes</processes> <!-- Database synchronization settings --> <synchronization> <max_eps>10</max_eps> </synchronization> </wodle>
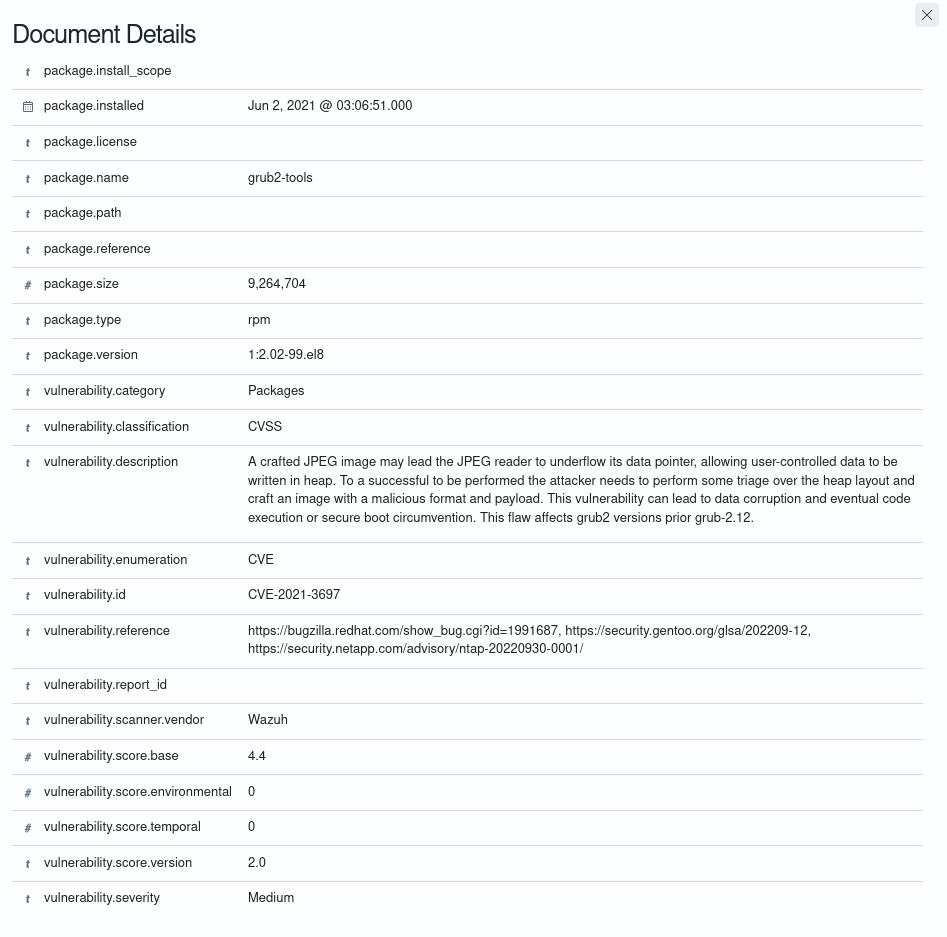
The Vulnerability Detection module generates logs in the ThreatLockDown server that trigger alerts. Every alert contains the following fields:
CVE: The Common Vulnerabilities and Exposures identifier for the corresponding vulnerability.
Rule description: Short description of the impact of the vulnerability.
Description: Broad description of the vulnerability.
Severity: Impact of the vulnerability in terms of security.
Package: Information about the affected package, including why the package is marked as vulnerable.
Enumeration: The enumeration reference.
Classification: The classification reference.
Reference: URL with extra information on the vulnerability.
You can see an alert sample below showing the fields with vulnerability data:
{
"_index": "wazuh-alerts-4.x-env-1-2024.01.04",
"_id": "5ZzO1IwBJcbqfTZ98NzR",
"_version": 1,
"_score": null,
"_source": {
"cluster": {
"node": "worker_01",
"name": "wazuh1"
},
"input": {
"type": "log"
},
"agent": {
"ip": "10.0.1.64",
"name": "Centos",
"id": "003"
},
"manager": {
"name": "wazuh-manager-worker-0"
},
"data": {
"vulnerability": {
"reference": "https://access.redhat.com/security/cve/cve-2022-3775, https://security.gentoo.org/glsa/202311-14",
"severity": "High",
"score": {
"environmental": "0",
"version": "3.1",
"temporal": "0",
"base": "7.100000"
},
"cve": "CVE-2022-3775",
"package": {
"installed": "2021-06-02T06:06:51.000Z",
"path": " ",
"size": "9264704",
"name": "grub2-tools",
"description": "Support tools for GRUB.",
"type": "rpm",
"version": "1:2.02-99.el8",
"architecture": "x86_64"
},
"scanner": {
"vendor": "Wazuh"
},
"description": "When rendering certain unicode sequences, grub2's font code doesn't proper validate if the informed glyph's width and height is constrained within bitmap size. As consequence an attacker can craft an input which will lead to a out-of-bounds write into grub2's heap, leading to memory corruption and availability issues. Although complex, arbitrary code execution could not be discarded.",
"category": "Packages",
"classification": "CVSS",
"enumeration": "CVE",
"status": "Active"
},
"aws": {
"accountId": "",
"region": ""
}
},
"rule": {
"firedtimes": 1752,
"mail": false,
"level": 10,
"pci_dss": [
"11.2.1",
"11.2.3"
],
"tsc": [
"CC7.1",
"CC7.2"
],
"description": "CVE-2022-3775 affects grub2-tools",
"groups": [
"vulnerability-detector"
],
"id": "23505",
"gdpr": [
"IV_35.7.d"
]
},
"location": "vulnerability-scanner",
"decoder": {
"name": "json"
},
"id": "1704377379.22094196",
"timestamp": "2024-01-04T14:09:39.845+0000"
},
"fields": {
"timestamp": [
"2024-01-04T14:09:39.845Z"
]
},
"highlight": {
"rule.groups": [
"@opensearch-dashboards-highlighted-field@vulnerability-detector@/opensearch-dashboards-highlighted-field@"
]
},
"sort": [
1704377379845
]
}
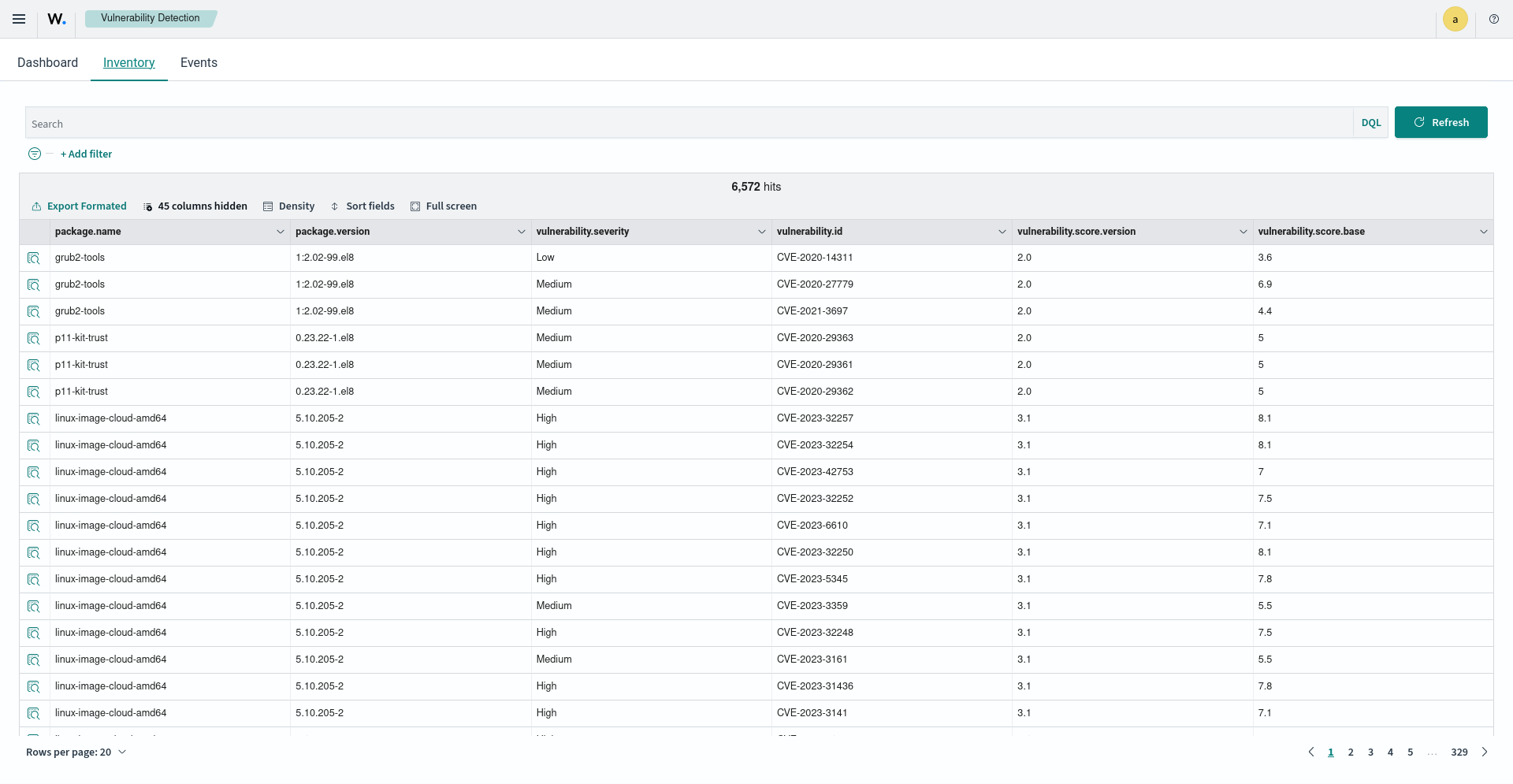
You can see the inventory of all the vulnerable packages installed for any agent by clicking on the Vulnerability Detection module on the ThreatLockDown dashboard.
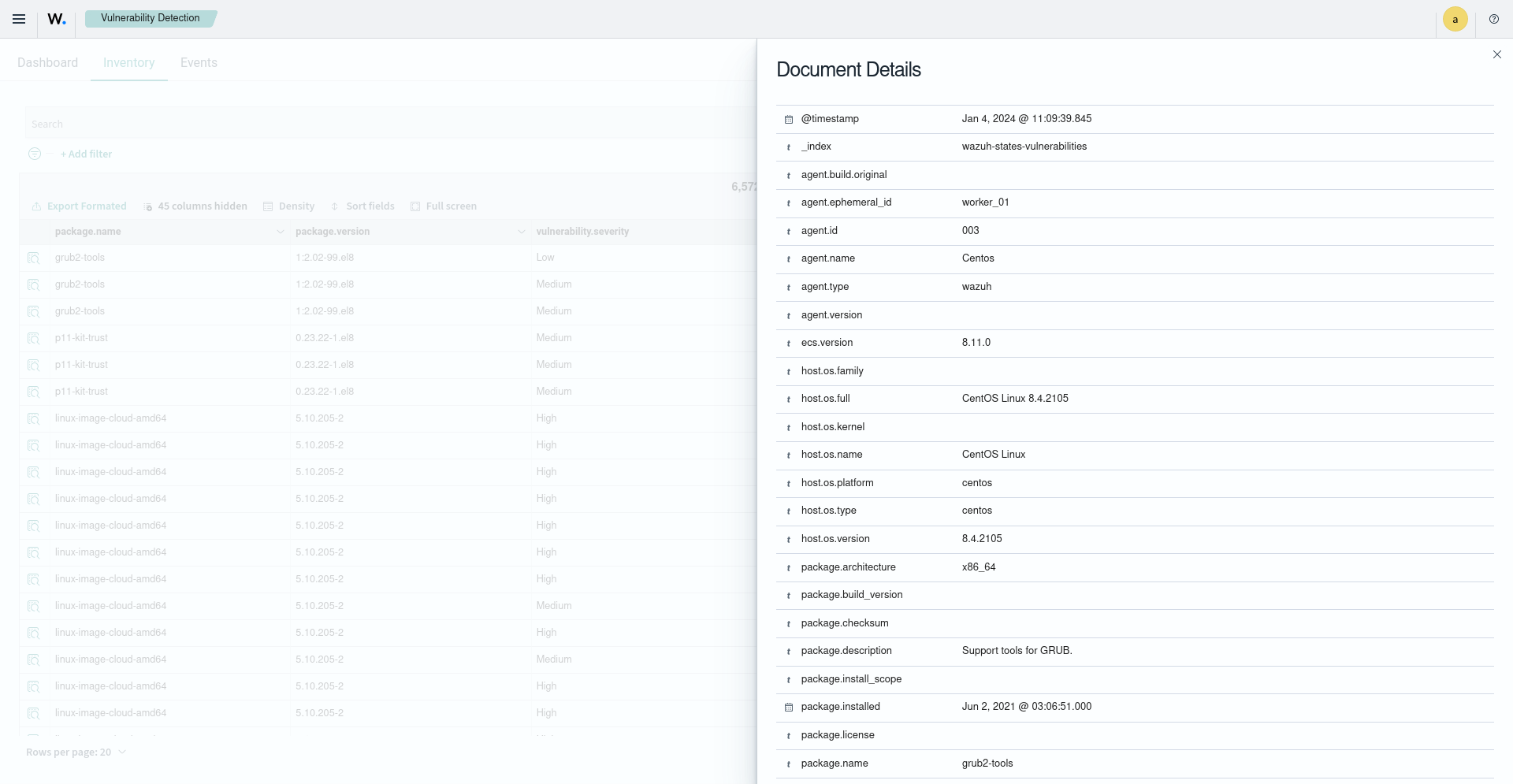
Here you can see what certain fields of the alert look like on the dashboard: