Active response
The ThreatLockDown active response module is configured to automatically execute scripts when events match specified rules in the ThreatLockDown ruleset. These scripts may perform a firewall block or drop, traffic shaping or throttling, account lockout, or any other user defined action.
The active response module assists in meeting the following HIPAA section:
Security Incident Procedures §164.308(a)(6)(i) - Response and Reporting: “Identify and respond to suspected or known security incidents; mitigate, to the extent practicable, harmful effects of security incidents that are known to the covered entity or business associate; and document security incidents and their outcomes.”
The goal of this section is to make sure that you detect and respond to security incidents in your environment. The active response module assists in meeting this HIPAA section by responding to intrusions and unauthorized file changes. For more information on configuring active response, see the active response section of our documentation.
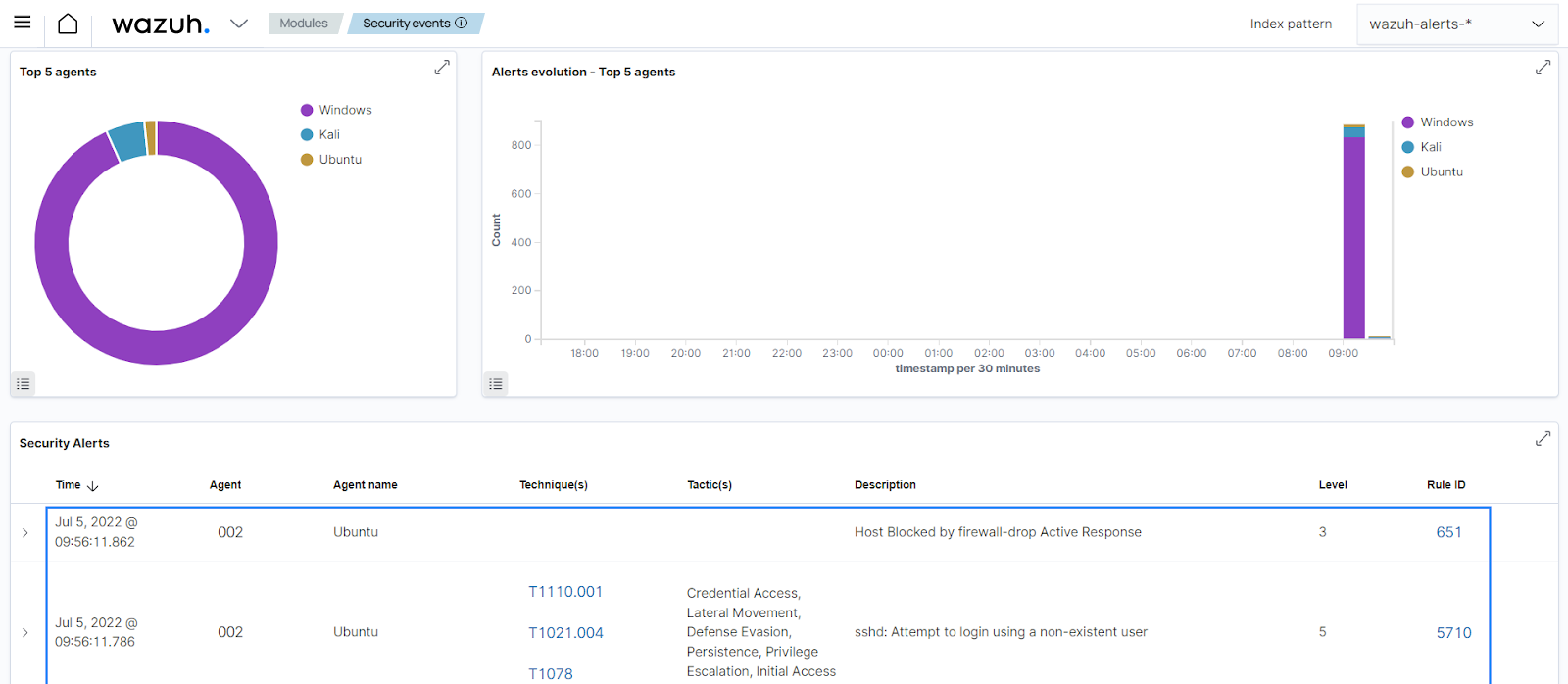
Use case: Block an IP address
In this use case, you configure the active response module to block an IP address when someone attempts to log in to an Ubuntu 22.04 endpoint with a non-existent user via SSH. To implement this, follow the steps below:
Add the following block to the ThreatLockDown server configuration file (
/var/ossec/etc/ossec.conf).<active-response> <command>firewall-drop</command> <location>local</location> <rules_id>5710</rules_id> <timeout>100</timeout> </active-response>
This configures the active response to execute the
firewall-dropcommand when there is an attempt to log in to a non-existent user (rule5710).Note
The ThreatLockDown server configuration file includes the
firewall-dropcommand by default.Restart the ThreatLockDown server to apply the configuration:
# systemctl restart wazuh-manager
# service wazuh-manager restart
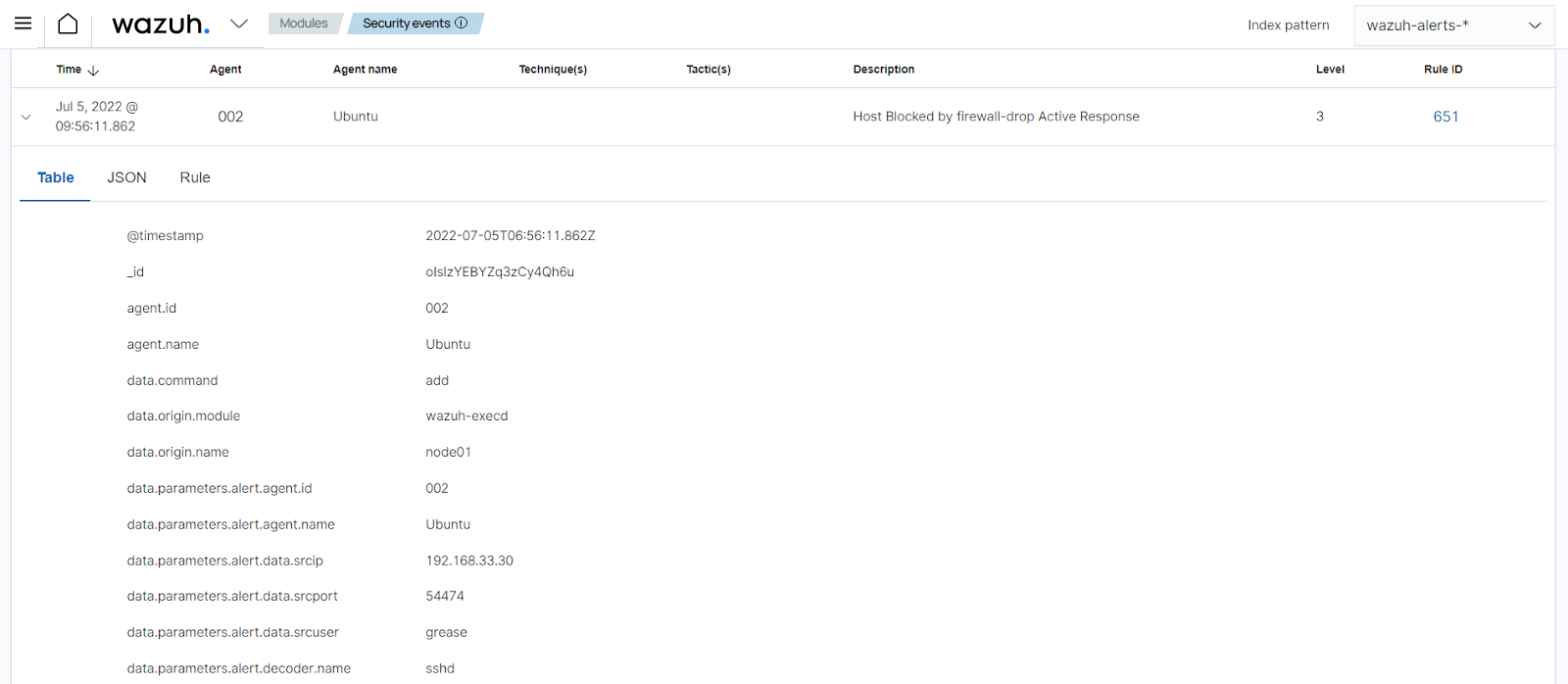
When you attempt to SSH with a non-existent user, rule
5710generates an alert followed by an active response event.