ThreatLockDown agent
The ThreatLockDown agent is multi-platform and runs on the endpoints that the user wants to monitor. It communicates with the ThreatLockDown server, sending data in near real-time through an encrypted and authenticated channel.
The agent was developed considering the need to monitor a wide variety of different endpoints without impacting their performance. It is supported on the most popular operating systems, and it requires 35 MB of RAM on average.
The ThreatLockDown agent provides key features to enhance your system’s security.
Log collector |
Command execution |
File integrity monitoring (FIM) |
Security configuration assessment (SCA) |
System inventory |
Malware detection |
Active response |
Container security |
Cloud security |
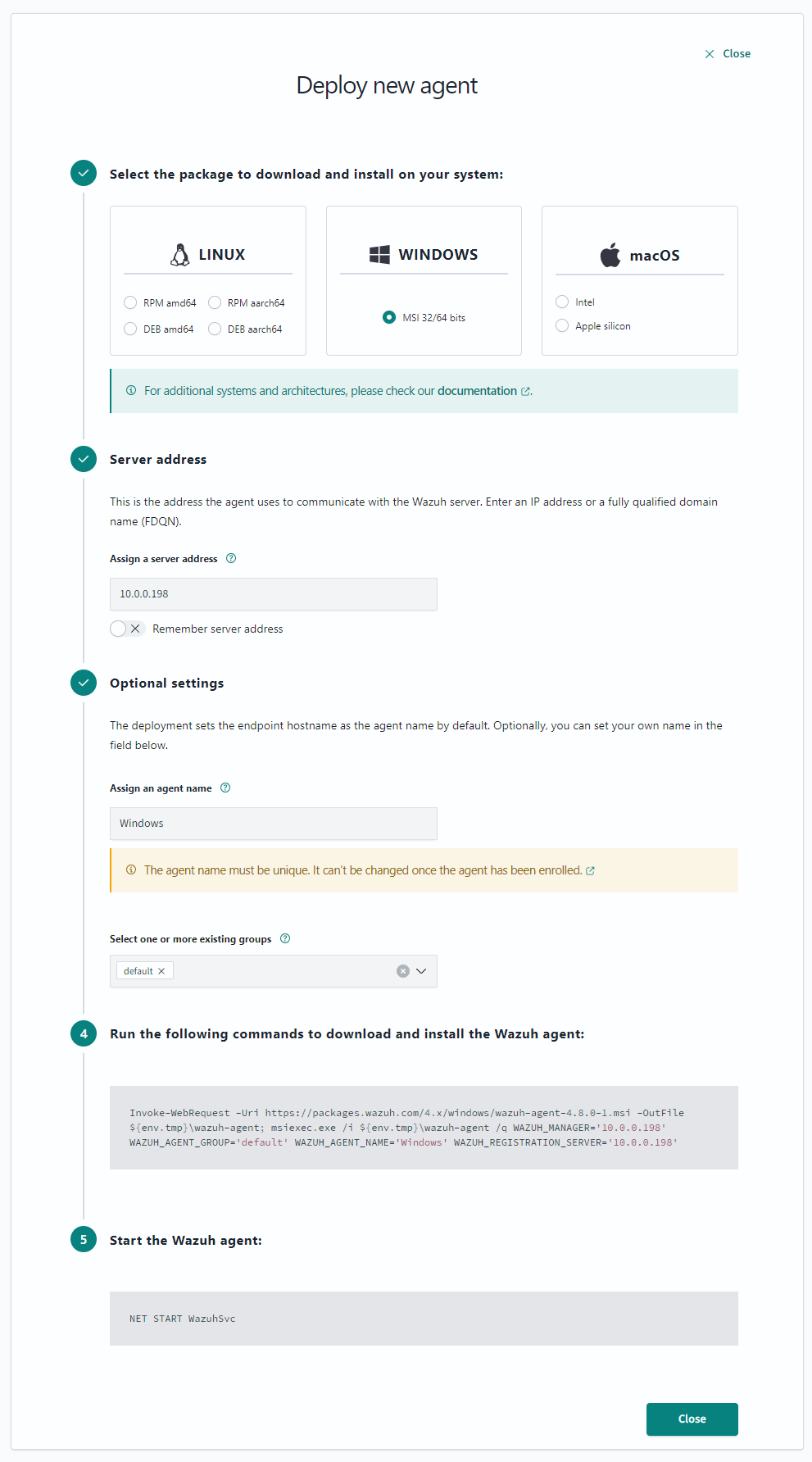
To install a ThreatLockDown agent, select your operating system and follow the instructions.
If you are deploying ThreatLockDown in a large environment, with a high number of servers or endpoints, keep in mind that this deployment might be easier using automation tools such as Puppet, Chef, SCCM, or Ansible.
Note
Compatibility between the ThreatLockDown agent and the ThreatLockDown manager is guaranteed when the ThreatLockDown manager version is later than or equal to that of the ThreatLockDown agent.
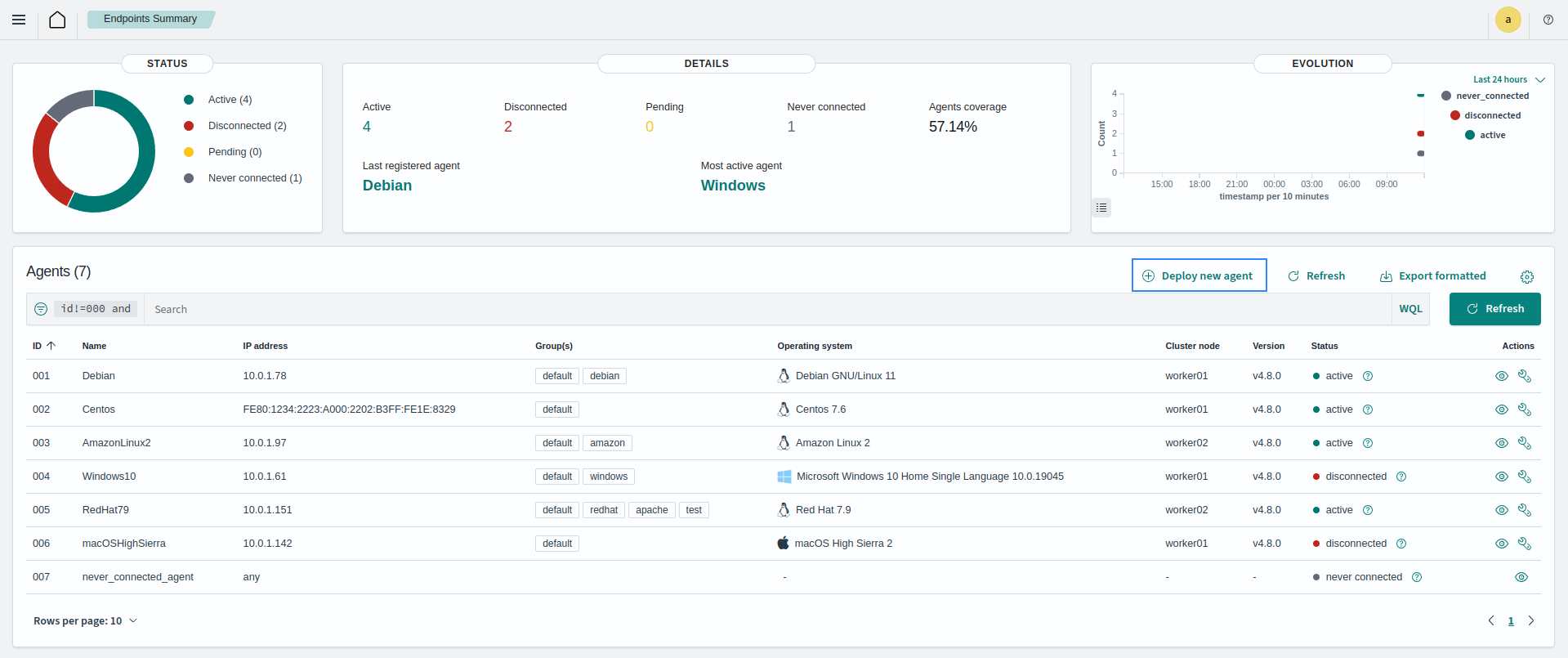
You can also deploy a new agent following the instructions in the ThreatLockDown dashboard. Go to Endpoints Summary, and click on Deploy new agent.
Then the ThreatLockDown dashboard will show you the steps to deploy a new agent.