Enhancing detection with MITRE ATT&CK framework
Created by the MITRE Corporation, MITRE ATT&CK is an acronym that stands for MITRE Adversarial Tactics, Techniques, and Common Knowledge. It is a globally-accessible collection of observed real-world threat actor actions and behavior. The MITRE ATT&CK framework describes 14 tactics and several techniques that security analysts can use to identify attacks in progress. MITRE uses IDs to reference the tactic or technique employed by an adversary.
The ThreatLockDown integration with MITRE ATT&CK framework is provided through an out-of-the-box module on the ThreatLockDown dashboard. It allows users to map alerts generated by ThreatLockDown to specific tactics and techniques. This gives security teams a better understanding of the nature of the threats they are facing and helps them develop effective mitigation strategies.
The ThreatLockDown MITRE ATT&CK module is accessible under the THREAT INTELLIGENCE section of the main page of the ThreatLockDown dashboard. It is shipped with various functionalities to help enhance your threat detection.
Intelligence
The Intelligence tab includes information about known threat actors or groups that have been observed using particular Tactics, Techniques, and Procedures (TTPs). It also provides any relevant indicators of compromise (IOCs) or mitigations that can be used to detect or prevent attacks leveraging the TTPs.
Additionally, it contains links to relevant external sources such as MITRE ATT&CK pages, blog posts, and white papers that provide detailed information about each TTP.
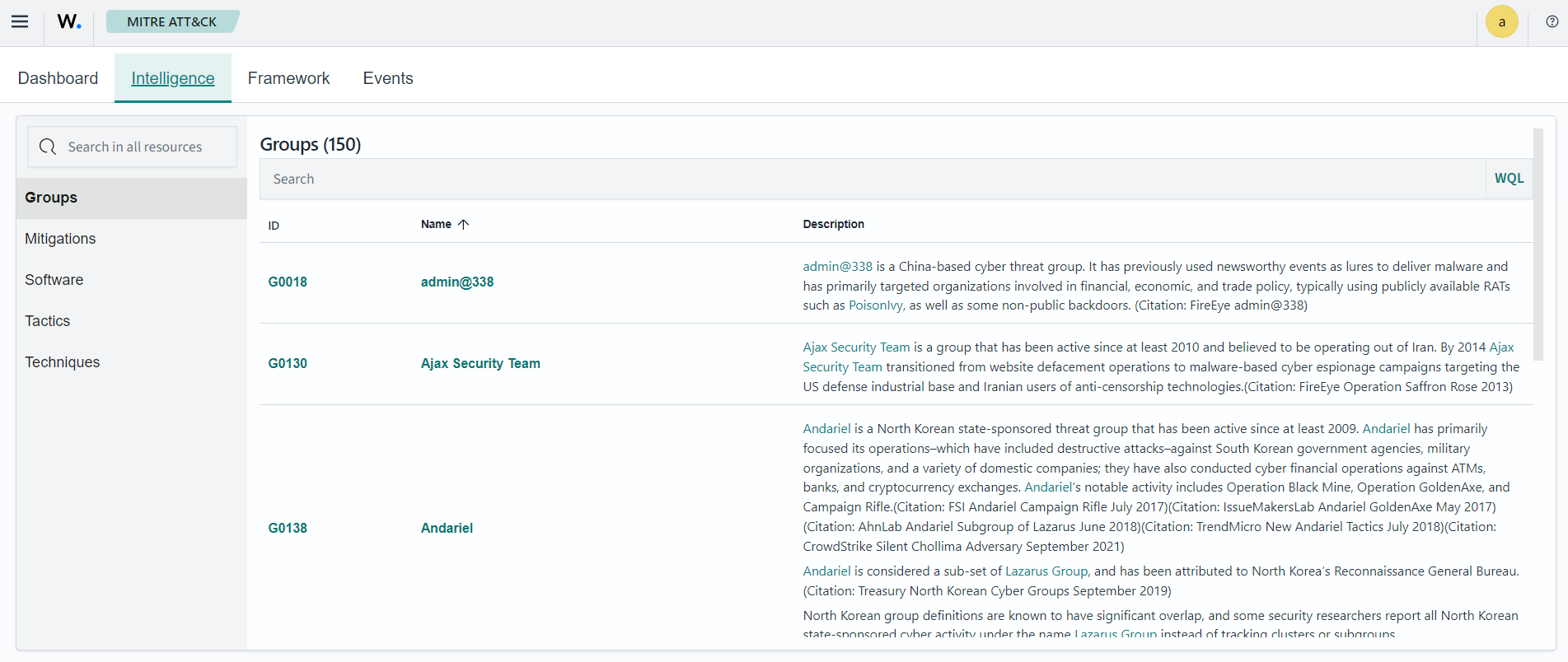
Framework
The Framework tab of the ThreatLockDown MITRE ATT&CK module provides a high-level overview of the tactics and techniques occurring in endpoints monitored by the ThreatLockDown server. This tab enables users to filter and search for specific tactics and techniques, and quickly view which endpoints these events occurred on. You can use this functionality to identify vulnerable areas in your environment.
Dashboard
This tab provides an overview of the current state of your infrastructure with respect to known adversarial Tactics, Techniques, and Procedures (TTPs) in the MITRE ATT&CK framework. The dashboard displays key indicators such as the total number of events, alerts, and a summary of the top 10 TTPs detected within your environment. These indicators can be used to assess the effectiveness of existing security controls and identify areas that may require further attention. Additionally, you can customize the dashboard to display specific metrics that are most relevant to your organization's security posture.
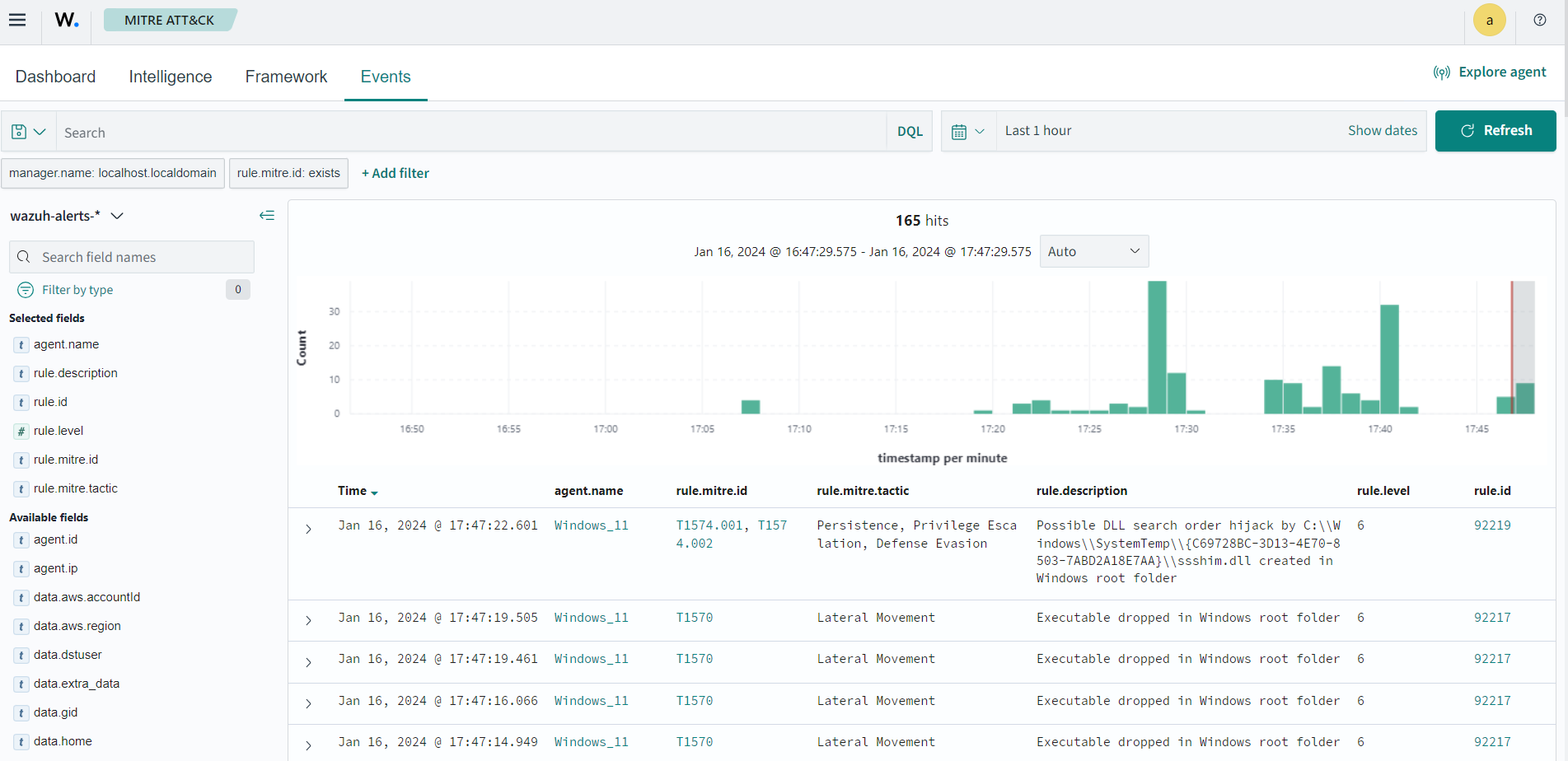
Events
This tab provides detailed information about each event that has been detected within your environment. It includes their correlation to specific TTPs as defined by the MITRE ATT&CK framework. The information shown in this tab is particularly useful for security teams who need to investigate suspicious activity. It allows them to drill down into the details of individual events and assess their potential impact on an environment.
You can filter the events based on various criteria such as severity, event type, and detection method, and also sort them by different fields to locate relevant information quickly. Additionally, the tab provides access to additional details, such as the full event log message and any related alerts that may have been generated in response to the event.
Customization
The ThreatLockDown MITRE ATT&CK module also supports a range of customization options. For example, users can define custom mappings between ThreatLockDown alerts and specific tactics and techniques, allowing them to tailor the module to their unique needs and requirements.
Customization example
ThreatLockDown has out-of-the-box detection rules that are mapped against relevant MITRE IDs. However, to use ThreatLockDown with MITRE ATT&CK for threat hunting, you can configure custom rules and assign corresponding MITRE ATT&CK IDs according to the number of techniques involved in the attack.
For this example, we require the following infrastructure:
Endpoint |
Example description |
|---|---|
ThreatLockDown server |
You can download the ThreatLockDown OVA or install it using the installation guide. |
Windows 11 |
We perform privilege escalation emulation attack on this endpoint.
It is required to have a ThreatLockDown agent installed and enrolled to the ThreatLockDown server. To install the ThreatLockDown agent, refer to the ThreatLockDown Windows installation guide.
|
ThreatLockDown server
Append the following rules to the
/var/ossec/etc/rules/local_rules.xmlfile:<group name="windows,sysmon,privilege-escalation"> <rule id="110011" level="10"> <if_sid>61615</if_sid> <field name="win.eventdata.targetObject" type="pcre2">HKLM\\\\System\\\\CurrentControlSet\\\\Services\\\\PSEXESVC</field> <field name="win.eventdata.eventType" type="pcre2">^SetValue$</field> <field name="win.eventdata.user" type="pcre2">NT AUTHORITY\\\\SYSTEM</field> <options>no_full_log</options> <description>PsExec service running as $(win.eventdata.user) has been created on $(win.system.computer)</description> <mitre> <id>T1543.003</id> </mitre> </rule> </group>
The rule
110011creates an alert whenever there is a creation of a service namedPSEXESVC, which occurs each time PsExec is executed on the Windows endpoint. It is mapped to the MITRE ATT&CK IDT1543.003, indicating the persistence and privilege escalation tactics.When the rule triggers, the alert contains information about the MITRE ATT&CK ID
T1543.003.Restart the ThreatLockDown manager service to apply the changes:
$ sudo systemctl restart wazuh-manager.service
Windows 11
Perform the following steps to configure the ThreatLockDown agent to capture Sysmon logs and send them to the ThreatLockDown server for analysis.
Download Sysmon and the configuration file sysmonconfig.xml.
Extract the contents of the
Sysmon.zipfile to a folder, and copy thesysmonconfig.xmlconfiguration file to the same folder.Launch PowerShell with administrative privilege, navigate to the folder used in the step above, and install Sysmon as follows:
> .\Sysmon64.exe -accepteula -i .\sysmonconfig.xml
Edit the ThreatLockDown agent
C:\Program Files (x86)\ossec-agent\ossec.conffile and include the following settings within the<ossec_config>block:<!-- Configure ThreatLockDown agent to receive events from Sysmon --> <localfile> <location>Microsoft-Windows-Sysmon/Operational</location> <log_format>eventchannel</log_format> </localfile>
Restart the ThreatLockDown agent for the changes to take effect:
> Restart-Service -Name wazuh
PsExec execution
We download the PsTools archive from the Microsoft Sysinternals page and extract the PsExec binary from the archive. The following command escalates a Windows PowerShell process from an administrator user to a SYSTEM user:
> .\psexec -i -s powershell /accepteula
Run the command below to confirm that the new instance of PowerShell is running as SYSTEM:
> whoami
Output is shown below:
PS C:\Windows\system32> whoami nt authority\system
Visualize the alerts
We use filters on the MITRE ATT&CK> Events tab of the ThreatLockDown dashboard to query for specific MITRE IDs, tactics, or techniques, as shown in the figure below.
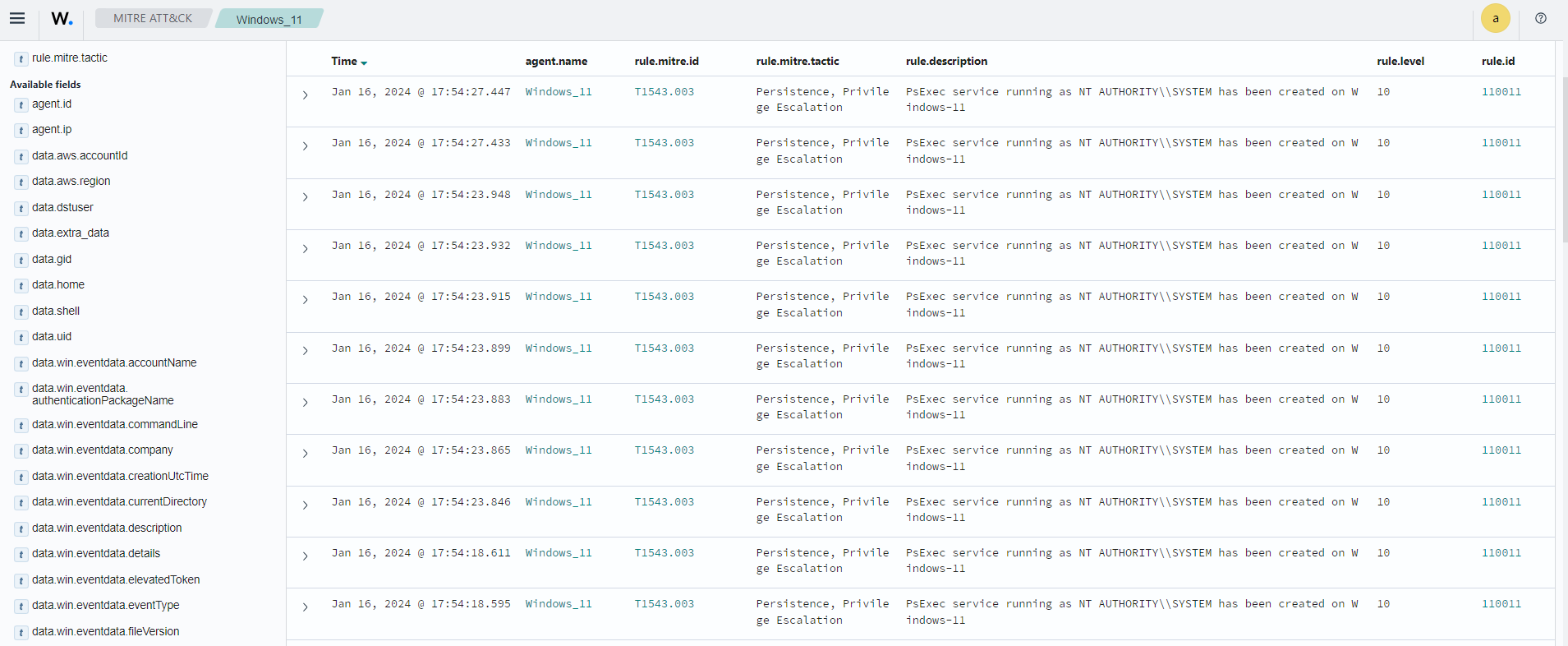
Expand the rule ID 110011 alert to view the MITRE ID T1543.003 information.
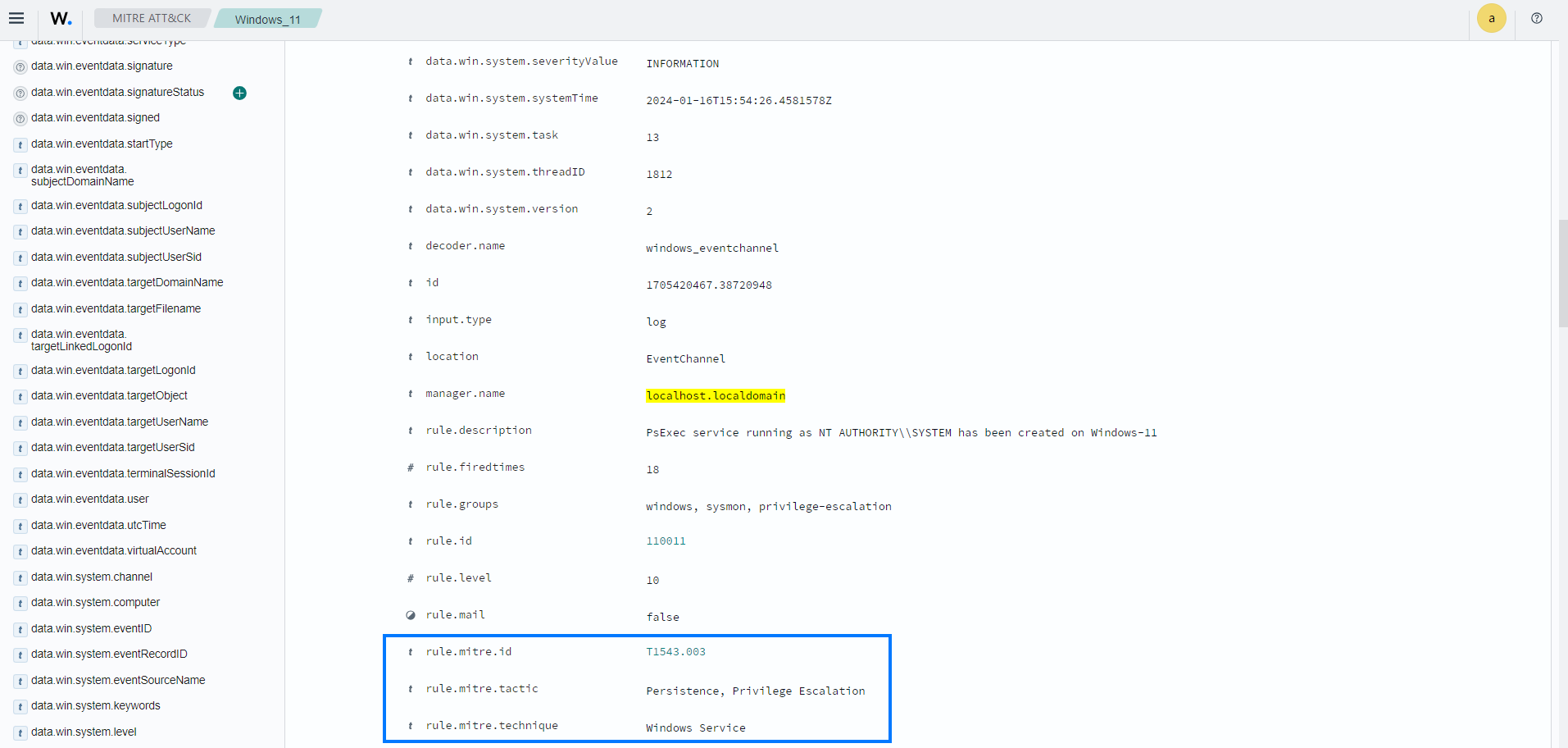
Click on the JSON tab to view the details of the alert in JSON format:
{
"agent": {
"ip": "10.0.2.15",
"name": "Windows_11",
"id": "001"
},
"manager": {
"name": "wazuh-server"
},
"data": {
"win": {
"eventdata": {
"image": "C:\\\\Windows\\\\system32\\\\services.exe",
"targetObject": "HKLM\\\\System\\\\CurrentControlSet\\\\Services\\\\PSEXESVC\\\\Start",
"processGuid": "{08d76baf-2978-65a7-0b00-000000001300}",
"processId": "708",
"utcTime": "2024-01-16 15:54:26.456",
"details": "DWORD (0x00000004)",
"eventType": "SetValue",
"user": "NT AUTHORITY\\\\SYSTEM"
},
"system": {
"eventID": "13",
"keywords": "0x8000000000000000",
"providerGuid": "{5770385f-c22a-43e0-bf4c-06f5698ffbd9}",
"level": "4",
"channel": "Microsoft-Windows-Sysmon/Operational",
"opcode": "0",
"message": "\"Registry value set:\r\nRuleName: -\r\nEventType: SetValue\r\nUtcTime: 2024-01-16 15:54:26.456\r\nProcessGuid: {08d76baf-2978-65a7-0b00-000000001300}\r\nProcessId: 708\r\nImage: C:\\Windows\\system32\\services.exe\r\nTargetObject: HKLM\\System\\CurrentControlSet\\Services\\PSEXESVC\\Start\r\nDetails: DWORD (0x00000004)\r\nUser: NT AUTHORITY\\SYSTEM\"",
"version": "2",
"systemTime": "2024-01-16T15:54:26.4581578Z",
"eventRecordID": "14864",
"threadID": "1812",
"computer": "Windows-11",
"task": "13",
"processID": "5908",
"severityValue": "INFORMATION",
"providerName": "Microsoft-Windows-Sysmon"
}
}
},
"rule": {
"firedtimes": 18,
"mail": false,
"level": 10,
"description": "PsExec service running as NT AUTHORITY\\\\SYSTEM has been created on Windows-11",
"groups": [
"windows",
"sysmon",
"privilege-escalation"
],
"mitre": {
"technique": [
"Windows Service"
],
"id": [
"T1543.003"
],
"tactic": [
"Persistence",
"Privilege Escalation"
]
},
"id": "110011"
},
"location": "EventChannel",
"decoder": {
"name": "windows_eventchannel"
},
"id": "1705420467.38720948",
"timestamp": "2024-01-16T15:54:27.447+0000"
}
The alerts display the MITRE ATT&CK ID and its associated tactics and techniques. This helps users quickly understand the nature of the attack and take appropriate actions.