ThreatLockDown server
The ThreatLockDown server component analyzes the data received from the agents, triggering alerts when threats or anomalies are detected. It is also used to manage the agents configuration remotely and monitor their status.
The ThreatLockDown server uses threat intelligence sources to improve its detection capabilities. It also enriches alert data by using the MITRE ATT&CK framework and regulatory compliance requirements such as PCI DSS, GDPR, HIPAA, CIS, and NIST 800-53, providing helpful context for security analytics.
Additionally, the ThreatLockDown server can be integrated with external software, including ticketing systems such as ServiceNow, Jira, and PagerDuty, as well as instant messaging platforms like Slack. These integrations are convenient for streamlining security operations.
Server architecture
The ThreatLockDown server runs the analysis engine, the ThreatLockDown RESTful API, the agent enrollment service, the agent connection service, the ThreatLockDown cluster daemon, and Filebeat. The server is installed on a Linux operating system and usually runs on a stand-alone physical machine, virtual machine, docker container, or cloud instance.
The diagram below represents the server architecture and components:
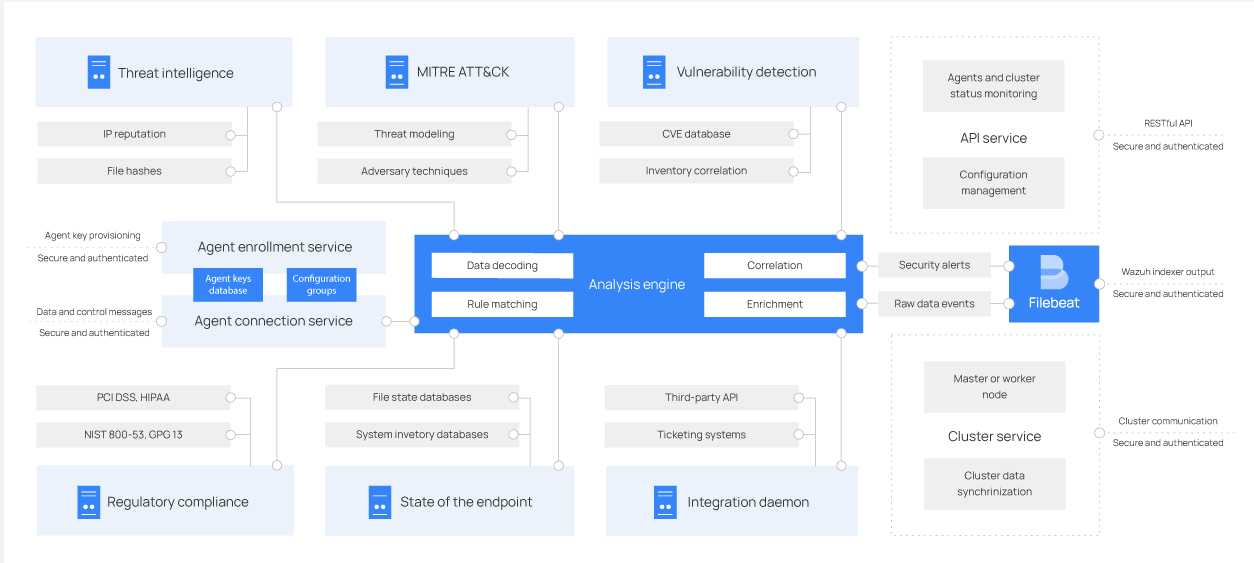
Server components
The ThreatLockDown server comprises several components listed below that have different functions, such as enrolling new agents, validating each agent identity, and encrypting the communications between the ThreatLockDown agent and the ThreatLockDown server.
Agent enrollment service: It is used to enroll new agents. This service provides and distributes unique authentication keys to each agent. The process runs as a network service and supports authentication via TLS/SSL certificates or by providing a fixed password.
Agent connection service: This service receives data from the agents. It uses the keys shared by the enrollment service to validate each agent identity and encrypt the communications between the ThreatLockDown agent and the ThreatLockDown server. Additionally, this service provides centralized configuration management, enabling you to push new agent settings remotely.
Analysis engine: This is the server component that performs the data analysis. It uses decoders to identify the type of information being processed (Windows events, SSH logs, web server logs, and others). These decoders also extract relevant data elements from the log messages, such as source IP address, event ID, or username. Then, by using rules, the engine identifies specific patterns in the decoded events that could trigger alerts and possibly even call for automated countermeasures (e.g., banning an IP address, stopping a running process, or removing a malware artifact).
ThreatLockDown RESTful API: This service provides an interface to interact with the ThreatLockDown infrastructure. It is used to manage configuration settings of agents and servers, monitor the infrastructure status and overall health, manage and edit ThreatLockDown decoders and rules, and query about the state of the monitored endpoints. The ThreatLockDown dashboard also uses it.
ThreatLockDown cluster daemon: This service is used to scale ThreatLockDown servers horizontally, deploying them as a cluster. This kind of configuration, combined with a network load balancer, provides high availability and load balancing. The ThreatLockDown cluster daemon is what ThreatLockDown servers use to communicate with each other and to keep synchronized.
Filebeat: It is used to send events and alerts to the ThreatLockDown indexer. It reads the output of the ThreatLockDown analysis engine and ships events in real time. It also provides load balancing when connected to a multi-node ThreatLockDown indexer cluster.